For the most part, I haven’t needed access to computers in my house while I’m away. All my files are stored in the cloud using Seafile. Seafile works a lot like Dropbox, so there are replicas of all my files sitting on my laptop. Always having my blog posts and OpenSCAD files with me on my laptop has almost entirely eliminated my need to access anything on my home network while I’m away.
Every now and then, though, I do need access to something at home. Maybe I need to take a peek at OctoPrint to see how a 3D print is going. Maybe I need access to OpenHAB or Home Assistant to check on my home automation.
The lazy thing to do might be to forward some ports to the OctoPrint and OpenHAB servers. This would get the job done, but these web interfaces aren’t really meant to be exposed to the Internet. All it would take is one vulnerability in either one, and someone would have access to everything on my home network. That’s not cool!
I used Wireguard for quite a while
A few years ago, I set up a Wireguard server on my OpenWRT router. It worked great! My aging router was fast enough to encrypt data at around 70 megabits per second. That’s less than half the speed of my 150/150 FiOS connection, but it is still plenty fast enough. My Linux laptop and Android phone had no trouble connecting, and everything worked great.
Getting things working with this setup on my Android phone was a bit of a hassle. The Wireguard port on the router wasn’t open to the local network, because I didn’t want my phone and laptop accidentally taking that extra hop over the encrypted link while in the house.
My phone needed to be able to send its battery percentage and charge status back to OpenHAB whether it was in the house or on the VPN. I believe I solved this problem the lazy way by just hard coding the OpenHAB server’s IP address in the OpenHAB app and Tasker.
Why did I stop using Wireguard?
One night, we had an outage. Either the power went out long enough that the UPS ran out of juice, or the Internet was just down and Chris power cycled the router to attempt to bring it back up. I can’t recall exactly what happened.
Something went weird that night. The router started giving the Wireguard interface a higher priority than the FiOS interface. I did some minimal troubleshooting, but it just didn’t want to come up cleanly. I implemented the lazy solution: I hit the disable button on Wireguard, went back to sleep, and figured I’d troubleshoot it another day.
That may have been almost two years ago, and I haven’t looked at it a single time since then. Being able to VPN home was nice, but in practice, I rarely used it.
What is Tailscale?
Tailscale is a service that allows you to connect all your computers to a single mesh network using the Wireguard protocol. Each device running Tailscale gets its own IP address on your Tailscale network, and every single device has its own Wireguard connection directly to every other device.
I enjoy Tailscale’s vision for their product. They want you to run Tailscale on every single network device that you own, and they want you to talk to every device on your network using Tailscale. If you do it their way, all traffic between every device on your network will always be encrypted using Wireguard.
You might think that since everyone at your company sits in the same office that this just doesn’t matter to you. Even so, it will matter to the handful of people that work remotely.
If Alice and Bob are collaborating on a project at Starbucks, Tailscale will make it seem like they’re still in the office. What’s so exciting about that? Most companies have a VPN, so they can already do this.
The neat thing about Tailscale is that Alice and Bob can communicate with each other securely and directly over the local network. They can quickly and easily share large files or Git repositories without the slow Starbucks Internet connection being a bottleneck.
Sure, you could have had most of the advantages of Tailscale for decades as long as your company had competent employees managing your network. Tailscale is a service that can get just about anyone to this point with very little work, and I think that’s awesome!
My Tailscale journey
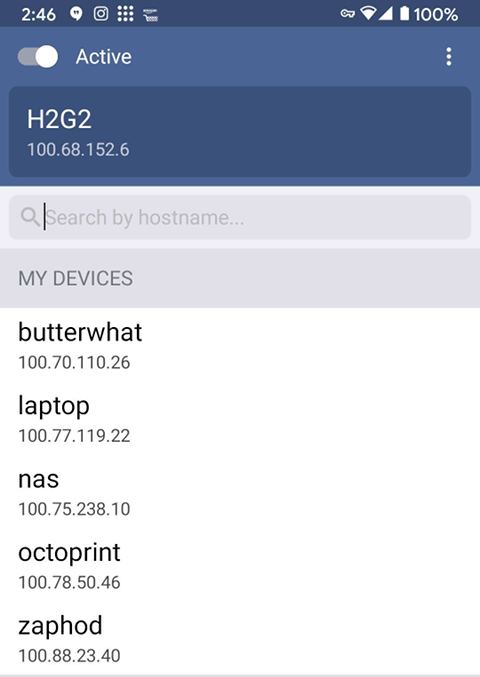
I’ve been slowly growing in to Tailscale. The first thing I did was set it up on my desktop, laptop, Android phone, and my little Windows 10 tablet. This was the extent of my installation for months, and I really didn’t get a chance to use it very often. I was home before the pandemic, and I’m home even more often these days!
Sometime later, I put my NAS virtual machine on Tailscale. When my new Prusa MK3S 3D printer arrived, I figured it was time to get OctoPrint onto my Tailscale network too!
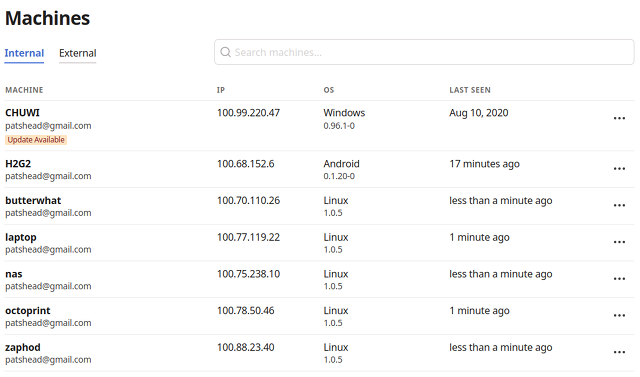
OctoPrint is the sort of thing that I set up and forget about. Sure, it has some pretty visualizations and webcam options, but at the end of the day all it really needs to do is pipe gcode over a serial port. When it is working, I don’t touch it.
Setting it up and forgetting about it meant that it was still running Ubuntu 16.04, and Tailscale doesn’t officially support this ancient Ubuntu release. It was easy enough to upgrade Ubuntu and install Tailscale.
This is where I am today, and it covers all the devices I currently need access to remotely.
Is Tailscale open-source?
No, but Tailscale has released an open-source client. I haven’t tried it. I’m using the closed-source build direct from Tailscale. It sounds like the code builds cleanly for Linux, and you may be able to make it work on the various BSDs and Windows.
An open-source Tailscale server is not available yet. It definitely looks like an open-source server implementation is on Tailscale’s roadmap.
Tailscale’s server is really only needed to help the client devices find each other and get connected. None of your network traffic passes through the Tailscale servers.
How much does Tailscale cost?
Tailscale is free for a single user and up to 100 devices. At the moment, though, I’m under the impression that many of the paid features are open to everyone. This may change at any time, though, so I wouldn’t rely too heavily on it!
The next tier is for teams, and it costs $10 per user per month. The tier above that bumps the device count to 500 devices, and the price goes up to $20 per user per month.
I’m just looking at Tailscale’s pricing page. I don’t know any more than you do, and I’m really only guessing about what some features in each bullet list actually means. If you need more advanced features than those available in the free plan, you should check out the pricing page.
Conclusion
I am a fan of Wireguard, and I am enjoying Tailscale. I bet it took less than 15 minutes to get Tailscale installed on two devices, and it doesn’t take more than 5 minutes to add another device. If you have no idea what you’re doing, it may take a bit longer, but I bet just about anyone could follow their simple directions.
What do you think? Are you using Tailscale? Do you prefer Zerotier? Would Tailscale solve some of your problems? Are you waiting for a completely open-source Tailscale implementation before you try it out? Wouldn’t Tailscale be a fantastic way for you to access your Home Assistant server remotely? Let me know in the comments, or stop by the Butter, What?! Discord server to chat with me about it!